Main menu
You are here
What is DMZ in networking
DMZ is short for DeMilitarized Zone.
In military jargon, a DMZ is an area of land that serves as a buffer between two enemies. The most well known DMZ in the world is the DMZ that protects South Korea from North Korea.
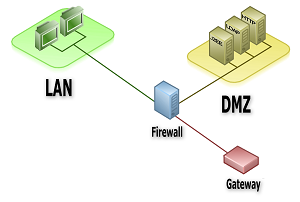
In network security jargon, a DMZ is a network that serves as a buffer between a secure protected internal network and the insecure Internet.
A DMZ usually contains servers which provide services to users from the Internet, such as web, ftp,
email (SMTP, POP3 and IMAP4), and DNS servers. Although these servers must be open to limited access from the Internet, they should also be protected by a firewall.

The term Perimeter Network is also used to describe a DMZ.
How to Create a DMZ
The most simple method of creating a DMZ is to utilize a firewall with three or more network interfaces. Each interface is assigned a specific role:
- Internal trusted network
- DMZ network
- External un-trusted network (the Internet)
Using a 4-port Ethernet card in your firewall will enable you to create a network in this configuration, or even enable you to create a network with two separate DMZ's.
Separating your DMZ hosts into multiple DMZ's will help to limit the damage that can be done if one of your DMZ hosts is compromised.
DMZ Firewall Rules
A firewall will normally be configured to protect the Internal network from the Internet.
To create a DMZ, the firewall should also enforce rules to protect the DMZ from the Internet and rules to protect the Internal network from the DMZ.
This will make it more difficult for an attacker to penetrate your Internal network, even if they do manage to gain access to your DMZ hosts.
source: topbits.com

