Main menu
You are here
Test your Wireless Security using WPA Cracker
Test your Wireless Security using WPA Cracker

Have you recently setup a wireless network for a small business or at home? For companies, making sure their wireless network is not hackable is very important, especially if sensitive data can be accessed.
Unfortunately, testing the security and strength of a wireless network is not very easy. To do it properly, you need the right equipment and right hacking software. If you know what you are doing, you can thoroughly test your wireless network for vulnerabilities and make the appropriate changes.
However, if you want to do some penetration testing on your wireless network without having to know very much technical information, WPA Cracker may be something to take a look at.
WPA Cracker (WEBSIDE LINK IS ATTACHED) is a cloud service that you can use for cracking and testing the security of WPA-PSK protected wireless networks.
So is this service free? Unfortunately, not! However, it’s really cheap and probably worth it for a small business that has sensitive data it would like to protect. If a hacker can gain access to your wireless network, they could potentially access all your servers and data.
What makes WPA Cracker special is the fact that you can run a dictionary attack against your WPA-PSK network using their 400 CPU cluster of servers. This means that you can run through a 135 million word dictionary in about 40 minutes using half the cluster or 20 minutes using the full cluster. That’s fast!!
The cost for using half of the CPU cluster is only $17 and for using the full cluster is $34. If you do this from a desktop computer, it could take an entire week. Who really has that much time to test the security of their network!
Also, if the service does not find your password, you still have to pay for running the test. However, your eventual goal is to make sure that the password cannot be cracked, so this result is good.
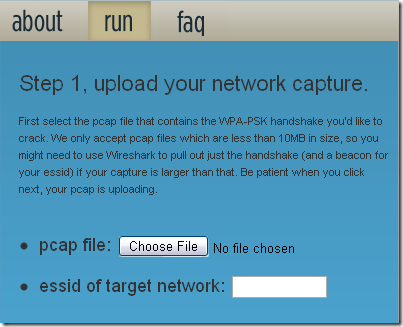
So exactly how does the WPA-PSK testing work? Luckily, it’s as simple as uploading a file to their servers! In order to run the test, you have to capture the WPA handshake. You can capture the handshake using software like Wireshark.
They also provide a link to a tutorial on using aircrack-ng to capture a WPA handshake. This is the only semi-difficult part in the whole process. However, once you capture the handshake, just click on run to upload the pcap file.
The file will have to be smaller than 10 MB, so make sure to only export the handshake. Plus, leave at least one beacon for your target network so that the handshake remains associated with the ESSID you want to target.
Overall, this is cloud computing at it’s best! It’s low-cost and very useful for performing brute-force type of tasks like this. If you want to make sure your wireless network cannot be hacked by a dictionary attack, check out WPA Cracker! Enjoy!
source: helpdeskgeek
| Attachment | Size |
|---|---|
| 36 bytes |